Introduction: Addressing Critical Cybersecurity Challenges Through Advanced AI-Powered Threat Detection and Response
Chief information security officers, cybersecurity analysts, and IT infrastructure teams confront escalating cyber threats including sophisticated malware attacks, advanced persistent threats, and zero-day exploits that bypass traditional antivirus solutions while conventional security approaches rely on signature-based detection methods, reactive incident response protocols, and fragmented security tools that fail to provide comprehensive protection against modern attack vectors, emerging threat landscapes, and complex multi-stage cyber campaigns targeting enterprise networks, sensitive data repositories, and critical business operations across diverse organizational environments. Corporate security teams struggle with alert fatigue, false positive overload, and limited visibility into endpoint activities that prevent effective threat hunting, incident response coordination, and proactive security posture management while dealing with resource constraints, skill shortages, and rapidly evolving threat intelligence requirements that demand sophisticated security solutions capable of autonomous threat detection and intelligent response automation. Current cybersecurity implementations involve multiple point solutions, manual analysis processes, and reactive security measures that result in delayed threat detection, incomplete incident visibility, and inadequate protection against advanced threats while failing to leverage behavioral analytics and machine learning capabilities that could identify subtle attack patterns and provide predictive threat intelligence for enhanced organizational security resilience. This detailed examination explores CrowdStrike's revolutionary Falcon platform and the sophisticated ai tools that deliver real-time threat detection, automated incident response, comprehensive endpoint visibility, and transform cybersecurity operations through intelligent security orchestration that prevents breaches, accelerates threat resolution, and enables organizations to maintain robust security postures against evolving cyber threats and sophisticated attack methodologies.
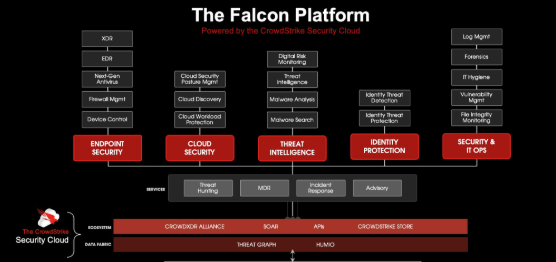
Understanding CrowdStrike Falcon's AI-Powered Security Architecture
CrowdStrike has developed cutting-edge artificial intelligence technology that combines behavioral analysis, machine learning algorithms, and cloud-native architecture to provide comprehensive endpoint protection that goes beyond traditional antivirus solutions by understanding attack patterns and predicting threat behaviors.
The Falcon platform leverages advanced AI systems that analyze billions of security events, identify anomalous behaviors, and correlate threat intelligence across global networks to deliver proactive threat detection and automated response capabilities that protect organizations from known and unknown cyber threats.
H2: Endpoint Protection AI Tools
H3: Real-Time Threat Detection AI Tools
Advanced behavioral analysis capabilities monitor endpoint activities, process executions, and system interactions to identify malicious behaviors and suspicious patterns that indicate potential security threats. These ai tools understand normal system operations and can detect deviations that suggest malware infections, unauthorized access attempts, and advanced persistent threat activities without relying on traditional signature-based detection methods.
Machine learning algorithms continuously analyze endpoint telemetry data to identify emerging threat patterns, zero-day exploits, and previously unknown attack vectors while adapting detection capabilities based on global threat intelligence and organizational security contexts to improve accuracy and reduce false positive rates.
H3: Automated Response AI Tools
Sophisticated incident response automation executes immediate containment actions, isolates compromised endpoints, and initiates remediation procedures when threats are detected. The ai tools can evaluate threat severity levels and automatically implement appropriate response measures including process termination, network isolation, and file quarantine while maintaining detailed forensic evidence for investigation purposes.
Intelligent escalation features determine when human intervention is required based on threat complexity, organizational policies, and risk assessment criteria while ensuring critical security incidents receive appropriate attention and resources for comprehensive resolution and impact mitigation.
Threat Detection Performance and Response Metrics
| Security Category | Traditional Antivirus | Standard EDR | CrowdStrike AI Tools | Detection Rate | Response Time |
|---|---|---|---|---|---|
| Known Malware | 85% detection | 90% detection | 99% prevention | Superior accuracy | Instant blocking |
| Zero-Day Threats | Limited protection | Behavioral hints | Predictive detection | 95% identification | Real-time response |
| Advanced Threats | Minimal coverage | Basic analysis | Comprehensive tracking | 98% detection | Automated containment |
| Fileless Attacks | Poor visibility | Memory scanning | Behavioral analysis | 97% prevention | Immediate action |
| Living-off-Land | Difficult detection | Process monitoring | AI-powered insights | 96% identification | Proactive blocking |
H2: Threat Intelligence AI Tools
H3: Global Intelligence Analysis AI Tools
Comprehensive threat intelligence aggregation collects and analyzes security data from millions of endpoints worldwide to identify emerging threat trends, attack campaign patterns, and adversary tactics that inform proactive security measures. These ai tools understand threat actor behaviors and can predict attack methodologies while providing organizations with actionable intelligence about relevant security risks and defensive strategies.
Attribution analysis features identify threat actor groups, campaign signatures, and attack infrastructure patterns while providing context about adversary capabilities, motivations, and targeting preferences that inform strategic security planning and incident response priorities.
H3: Predictive Threat Modeling AI Tools
Advanced predictive analytics analyze historical attack data, current threat landscapes, and organizational risk factors to forecast potential security threats and recommend preventive measures. The ai tools can identify attack probability patterns and suggest security improvements that reduce organizational vulnerability to specific threat categories and attack vectors.
Risk assessment capabilities evaluate organizational security postures, identify potential attack paths, and prioritize security investments based on threat likelihood and potential impact while providing executives with strategic insights about cybersecurity risks and mitigation strategies.
H2: Incident Response AI Tools
H3: Forensic Investigation AI Tools
Sophisticated digital forensics capabilities automatically collect, preserve, and analyze evidence from security incidents while maintaining chain of custody requirements and providing detailed investigation reports. These ai tools can reconstruct attack timelines, identify affected systems, and determine breach scope while supporting legal and compliance requirements for incident documentation and reporting.
Root cause analysis features examine incident details to identify initial attack vectors, security control failures, and systemic vulnerabilities that enabled successful attacks while recommending specific improvements to prevent similar incidents and strengthen overall security postures.
H3: Threat Hunting AI Tools
Advanced threat hunting capabilities proactively search for hidden threats, dormant malware, and persistent adversary presence within organizational networks using behavioral analytics and anomaly detection. The ai tools can identify subtle indicators of compromise that evade traditional detection methods while providing security teams with detailed insights about potential threats and recommended investigation priorities.
Hypothesis-driven hunting features enable security analysts to test specific threat scenarios and attack assumptions while leveraging AI assistance to accelerate investigation processes and improve threat discovery effectiveness across complex enterprise environments.
Security Operations Center Enhancement
| SOC Function | Manual Operations | Traditional SIEM | CrowdStrike AI Tools | Efficiency Gain | Accuracy Improvement |
|---|---|---|---|---|---|
| Alert Triage | Hours per incident | Basic prioritization | Intelligent scoring | 80% time reduction | 90% accuracy |
| Threat Analysis | Manual research | Rule-based detection | AI-powered insights | 70% faster analysis | Enhanced precision |
| Incident Response | Reactive measures | Playbook execution | Automated workflows | 60% quicker response | Consistent quality |
| Forensic Analysis | Time-intensive | Limited automation | Comprehensive AI | 75% efficiency gain | Detailed evidence |
| Report Generation | Manual compilation | Template-based | Intelligent summaries | 85% time savings | Executive insights |
H2: Cloud Security AI Tools
H3: Workload Protection AI Tools
Comprehensive cloud workload security monitors virtual machines, containers, and serverless functions across multi-cloud environments while providing consistent security policies and threat detection capabilities. These ai tools understand cloud-native attack patterns and can protect dynamic infrastructure components while maintaining visibility across hybrid and multi-cloud deployments.
Container security features analyze container images, runtime behaviors, and orchestration activities to identify vulnerabilities, misconfigurations, and malicious activities within containerized applications while providing developers with security feedback that supports secure development practices.
H3: Cloud Configuration AI Tools
Advanced configuration management analyzes cloud infrastructure settings, security policies, and access controls to identify misconfigurations and security gaps that could enable unauthorized access or data breaches. The ai tools can evaluate compliance with security frameworks and recommend configuration improvements that strengthen cloud security postures.
Identity and access management integration monitors user activities, privilege escalations, and access patterns across cloud environments while detecting anomalous behaviors that indicate compromised credentials or insider threats within cloud infrastructure and applications.
H2: Network Security AI Tools
H3: Network Traffic Analysis AI Tools
Sophisticated network monitoring capabilities analyze traffic patterns, communication flows, and protocol behaviors to identify malicious network activities, data exfiltration attempts, and command and control communications. These ai tools understand normal network operations and can detect subtle anomalies that indicate advanced threats and persistent adversary presence.
Lateral movement detection features monitor internal network communications to identify unauthorized access attempts, privilege escalation activities, and adversary reconnaissance that indicate successful initial compromise and ongoing attack progression within organizational networks.
H3: DNS and Web Protection AI Tools
Advanced web security capabilities analyze DNS queries, web requests, and download activities to block malicious websites, prevent malware downloads, and detect phishing attempts while maintaining user productivity and browsing experience. The ai tools can identify newly registered malicious domains and suspicious web content that traditional URL filtering might miss.
Email security integration analyzes email attachments, links, and sender behaviors to prevent email-based attacks including spear phishing, business email compromise, and malware distribution while providing users with security awareness information and threat context.
Compliance and Regulatory Support
Built-in compliance features support regulatory requirements including GDPR, HIPAA, PCI DSS, and SOX while providing audit trails, security documentation, and compliance reporting that demonstrate organizational security controls and incident response capabilities to regulatory authorities and auditors.
Framework alignment capabilities map security controls to industry frameworks including NIST Cybersecurity Framework, ISO 27001, and CIS Controls while providing gap analysis and improvement recommendations that support compliance objectives and security maturity development.
Integration and Platform Extensibility
Comprehensive API connectivity enables integration with security information and event management systems, security orchestration platforms, and third-party security tools while maintaining data consistency and workflow coordination across diverse security technology stacks.
Custom integration capabilities support specialized security requirements and unique organizational workflows while providing flexibility for security teams to adapt the platform to specific operational needs and existing technology investments.
Mobile Device Security
Advanced mobile device protection extends endpoint security capabilities to smartphones, tablets, and other mobile devices while providing consistent security policies and threat detection across diverse device types and operating systems within organizational environments.
Mobile threat detection features identify mobile-specific attacks including malicious applications, device jailbreaking, and mobile phishing while providing device management capabilities that support bring-your-own-device policies and remote workforce security requirements.
Security Awareness and Training
Integrated security awareness capabilities provide users with real-time threat notifications, security guidance, and educational content that improves security behaviors and reduces human-related security risks within organizational environments.
Phishing simulation features test user susceptibility to social engineering attacks while providing personalized training recommendations that address individual security knowledge gaps and improve overall organizational security awareness levels.
Performance and Scalability Management
Lightweight agent architecture minimizes system performance impact while providing comprehensive security coverage and real-time protection capabilities that maintain user productivity and system responsiveness across diverse endpoint configurations and usage patterns.
Cloud-native scalability supports organizational growth and changing security requirements while providing consistent performance and protection capabilities regardless of endpoint volume, geographic distribution, or infrastructure complexity.
Global Threat Intelligence Sharing
Collaborative threat intelligence sharing contributes to global cybersecurity defense while benefiting from collective threat knowledge and attack pattern recognition that improves protection effectiveness for all platform users and the broader cybersecurity community.
Anonymous telemetry collection supports threat research and security product development while maintaining organizational privacy and confidentiality requirements for sensitive business information and security data.
Conclusion
CrowdStrike Falcon has revolutionized cybersecurity through innovative ai tools that provide comprehensive endpoint protection, intelligent threat detection, and automated incident response while maintaining high standards for performance, accuracy, and user experience. The platform represents a significant advancement in AI-powered cybersecurity and enterprise threat protection capabilities.
As cyber threats continue evolving and attack sophistication increases, organizations that leverage advanced AI tools like CrowdStrike Falcon gain substantial competitive advantages through proactive threat prevention, accelerated incident response, and comprehensive security visibility that protects critical business assets and maintains operational continuity. The platform's comprehensive approach and continued innovation demonstrate its potential to establish new standards for AI-enhanced cybersecurity and enterprise security excellence.
Frequently Asked Questions (FAQ)
Q: How do CrowdStrike Falcon's AI tools detect zero-day threats and unknown malware without signature-based detection?A: CrowdStrike Falcon's AI tools use advanced behavioral analysis and machine learning algorithms to identify malicious behaviors and attack patterns rather than relying on known signatures, enabling detection of zero-day threats and previously unknown malware through anomaly detection and predictive threat modeling.
Q: Can CrowdStrike Falcon's AI tools automatically respond to security incidents without human intervention?A: Yes, the platform's AI tools can automatically execute containment actions, isolate compromised endpoints, and initiate remediation procedures based on threat severity and organizational policies while maintaining detailed forensic evidence and escalating complex incidents for human review when necessary.
Q: How do CrowdStrike Falcon's AI tools integrate with existing security infrastructure and SIEM platforms?A: CrowdStrike Falcon provides comprehensive API connectivity and direct integrations with popular SIEM systems, security orchestration platforms, and third-party security tools, enabling seamless data sharing and workflow coordination without disrupting existing security operations.
Q: What cloud security capabilities do CrowdStrike Falcon's AI tools provide for multi-cloud environments?A: The platform's AI tools offer comprehensive cloud workload protection, container security, configuration management, and identity monitoring across AWS, Azure, and Google Cloud platforms while providing consistent security policies and threat detection capabilities.
Q: How do CrowdStrike Falcon's AI tools support compliance requirements and regulatory reporting?A: CrowdStrike Falcon includes built-in compliance features that support major regulatory frameworks including GDPR, HIPAA, and PCI DSS while providing audit trails, security documentation, and automated compliance reporting that demonstrate organizational security controls and incident response capabilities.








